Status of This Document
This document is an incomplete draft. The sections that have been incorporated have been reviewed following the SafeTogether [Process]. However, the information in this document is still subject to change.You are invited to contribute any feedback, comments, or questions you might have.
Contributors
Many people contributed to this specification; here is an incomplete list (please contact editor to add your name in this list):
-
Andrea Carmignani
-
Luca Merealli
-
Luca Mastrostefano
-
Luciano Baresi
Many thanks to all contributors in GitHub
1. Tracing System
These documents SHOLUD be taken into consideration for tracing domain :
**Note that DP-3T is not PEEP-PT**
Note: to say that a standard/protocol/specification must be taken into consideration, does not means that you have to adopt it, but it states that you know it and you are able to describe why you adopt it or not.
The Tracing reference application is made by the Covid Community Alert Team, the source code is available with open source license.
The architecture and the protocols for the Covid Community Alert reference application is described in the project documentation
Here are some protocol interactions:
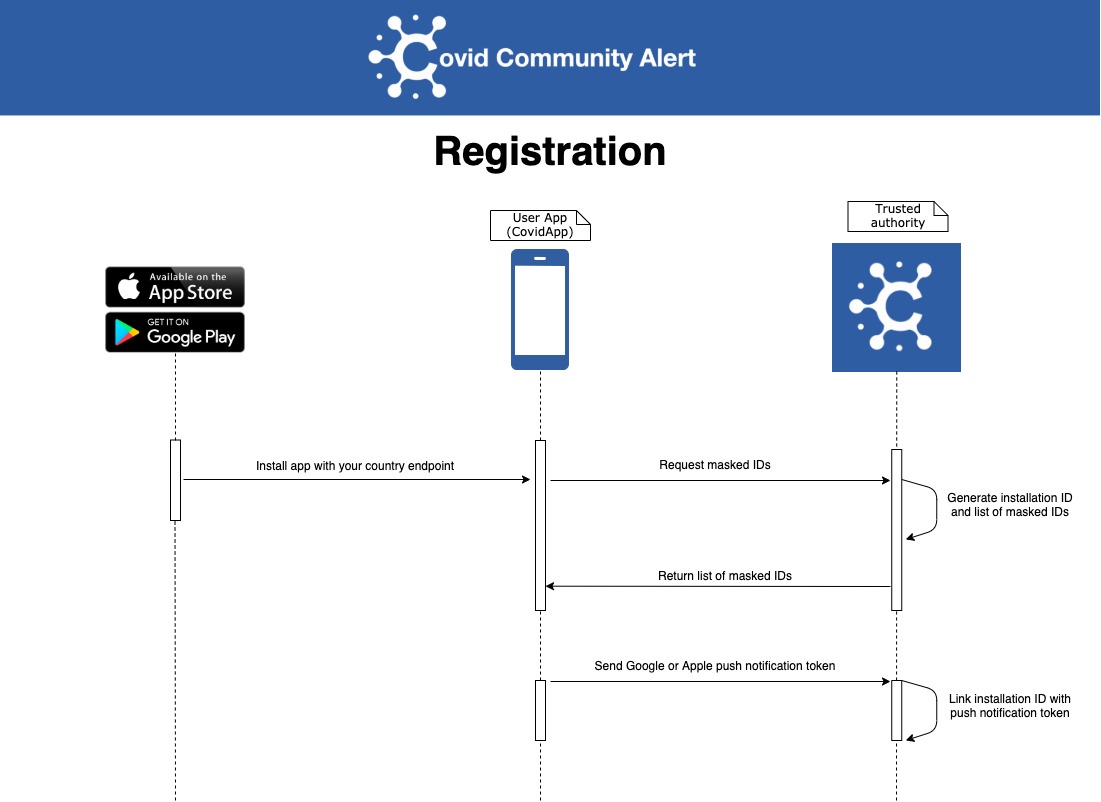
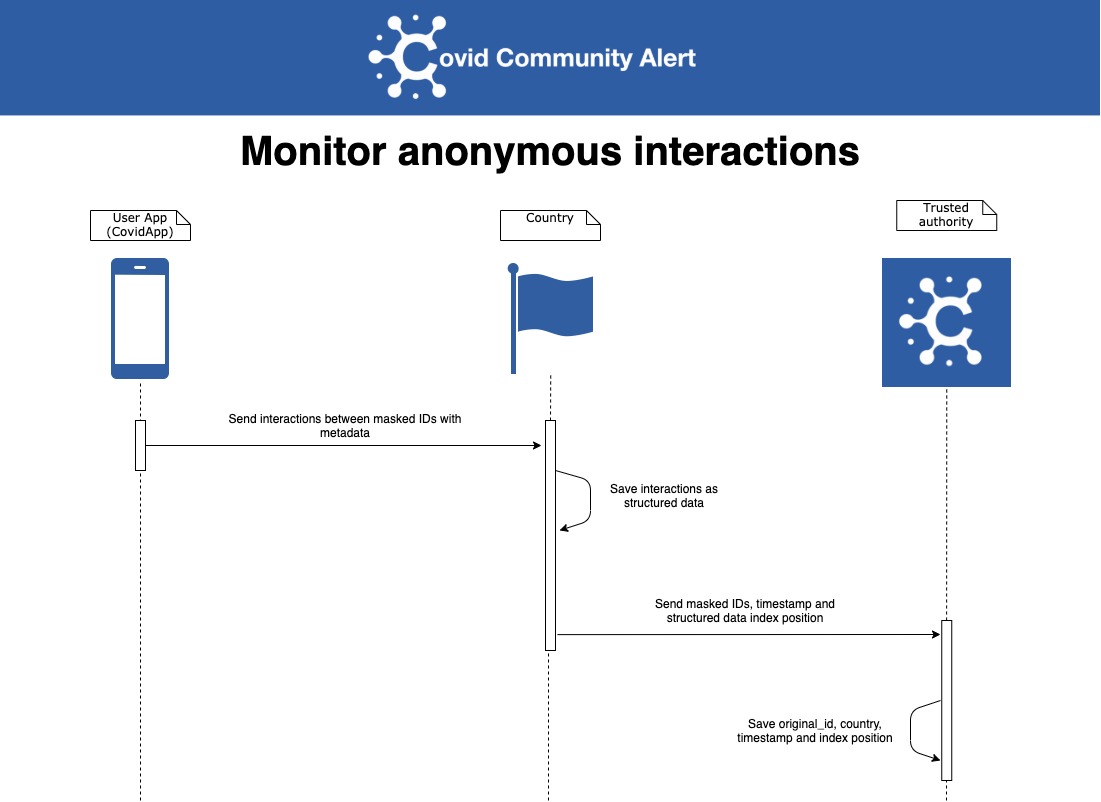
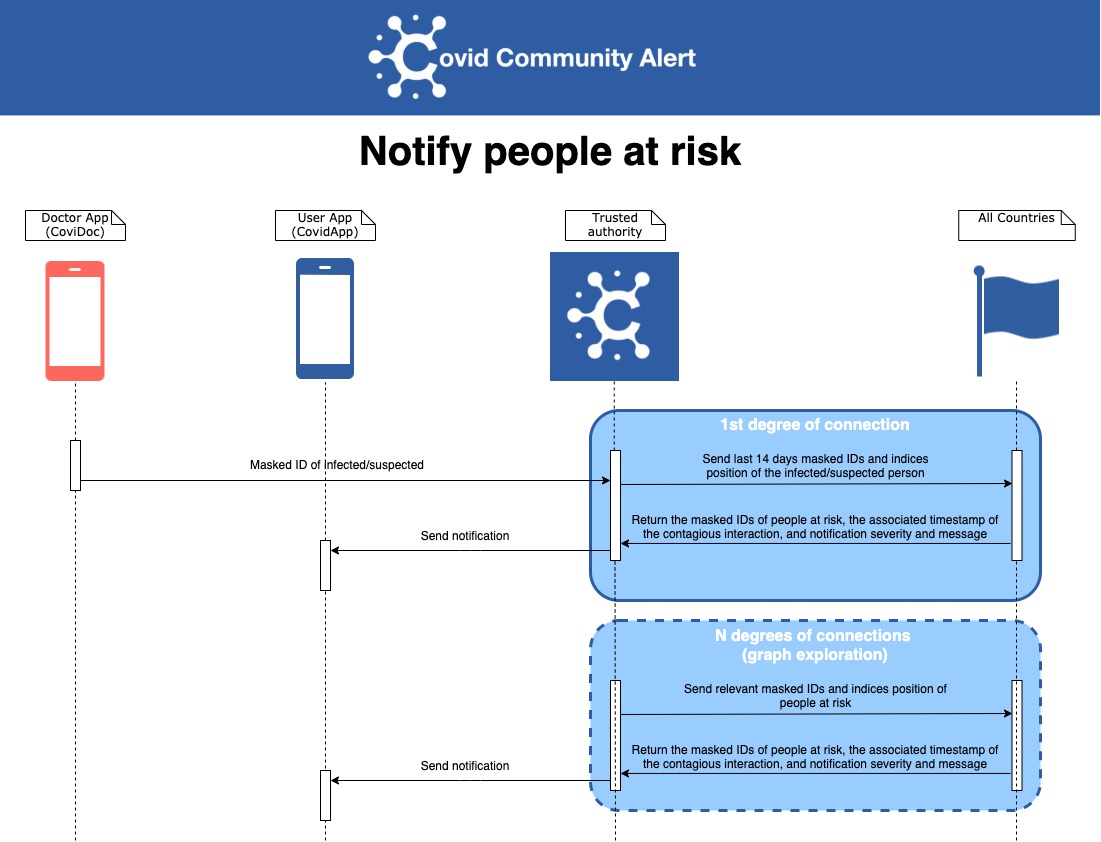
2. Quarantine System
The Quarantine reference implementation is made by Keyless team using its zero knowledge biometric authentication see keyless resources
The source repository with Free Open Source License is available on request contacting covid@keyless.io.
3. Shielding System
The Shielding system adopts following standards and frameworks:
-
[verifiableCredentials] for credential definition standard made by W3C
-
[indy] a reference implementation for Self Sovereign Identity (SSI)
-
[aries] a shared, reusable, interoperable tool kit designed for initiatives and solutions focused on creating, transmitting and storing verifiable digital credentials
-
The Sovrin Foundation as an open source specification framework that implements SSI
-
The CovidCreds that propose a shared format for Covid Relate Verifiable Credential.
The Shielding reference implementation is made by g0v.it team using the DIZME platform kindly provided by Infocert
The architecture and the protocols for Shielding Reference application is described in the Shielding Project repository documentation
The main components of the Shielding System are summarized in following picture:
